An introduction to Information Gathering
Information Gathering is the first step in penetration testing, and is also the most crucial part in the whole process itself, and every successful operation will heavily depend on it. This phase consistes of collecting all possible type of information about a given target. Any information whatever irrelevant it may seem, can be of the utmost importance. This includes network address range, live hosts, open ports and the services running on these ports, operating systems,and you can also collect emails or phone numbers that can be used later on for social engineering purposes.
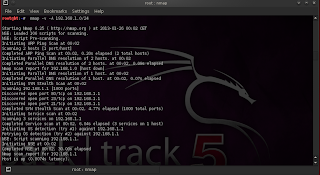
A big arsenal of tools is available for the reconnaissance phase and they are pre- installed in Backtrack. We cannot talk about Information gathering without mentioning nmap (Network Mapper). It is in fact a flexible and powerful utility for network discovery and security auditing.
figure 1: nmap in action
figure 2: nmap in action
Other alternatives for nmap are zenmap, dnmap, netifera, netcat and a dozen of other useful tools like dmitry. (i already posted a tutorial about Dmitry, if you are intersted, here is the link: http://backtrack-wifu.blogspot.com/2013/01/dmitry-footprinting-tool.html).
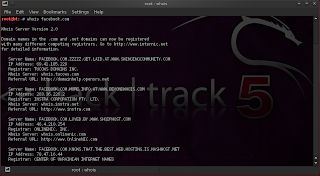
We can also start with a dns lookup.
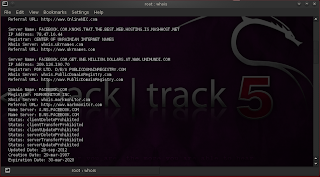
figure3: performing a whois lookup on facebook
figure 4: more whois data about facebook
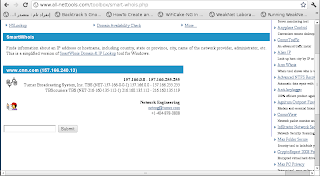
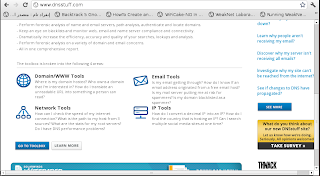
I f you are that lazy, you can rely on online tools. A useful site for this purpose is: http://www.all-nettools.com/ which is of great help for beginners. It provides a lot of services like: whois lookup, tracerouting, nslookup etc...
figure 5: list services in all-net-tools
figure6: smart whois on cnn.com
You may also try http://www.dnsstuff.com/
figure 7: available service in dnsstuff.com
figure 8: performing an ip traceroute
To the surprise of many people, one of the first information gathering sources for a pentester is GOOGLE !! It can reveal a lot of valuable information that people may not want us to discover. This is possible with what is referred to as google hacks.
Let's look for a private directory for example:
figure 9: google hacks
figure 10: google hacks
You can also use other tools to trace email senders or for IDS or IPS identification. The only thing that you have to bear in mind, is that information gathering is an art, and if you master this art, everything else would be much easier. Another important thing here worth mentioning, which is documentation. This step consists of having a good and organized documentation for your findings. A lot of tools are also available for this task like: casefile,magictree and basket. I am going to post some tutorials about information gathering tools, and documentation tools as soon as possible. Hope you enjoyed.
TO BE CONTINUED






0 commentaires: